Source: CertiK Chinese Community
CertiK recently discovered a series of serious vulnerabilities in Kraken Exchange that could potentially result in hundreds of millions of dollars in losses.
Overview of the incident
Starting with the discovery that the Kraken Exchange deposit system may not be able to distinguish between different internal transfer states, CertiK conducted a comprehensive investigation and raised three key questions:
Can malicious actors forge a deposit transaction to a Kraken account?
Can malicious actors withdraw forged funds?
What risk controls and asset protection measures are triggered in the case of large withdrawal requests?
According to the test results, Kraken Exchange failed all of these tests, indicating that Kraken's defense-in-depth system was compromised in multiple aspects; Millions of dollars can be deposited into any Kraken account. Large amounts of forged cryptocurrency (worth more than $1 million) can be withdrawn from accounts and converted into valid cryptocurrency. Worse still, no alerts were triggered during the multi-day testing period. Kraken responded and locked the test account days after we formally reported the incident.
Upon discovery, CertiK notified Kraken, whose security team classified it as “Critical”: Kraken’s most severe classification. After initially successfully identifying and fixing the vulnerability, Kraken’s security operations team threatened individual CertiK employees to repay unmatched amounts of cryptocurrency in an unreasonable amount of time, without even providing a repayment address.
Details Disclosure
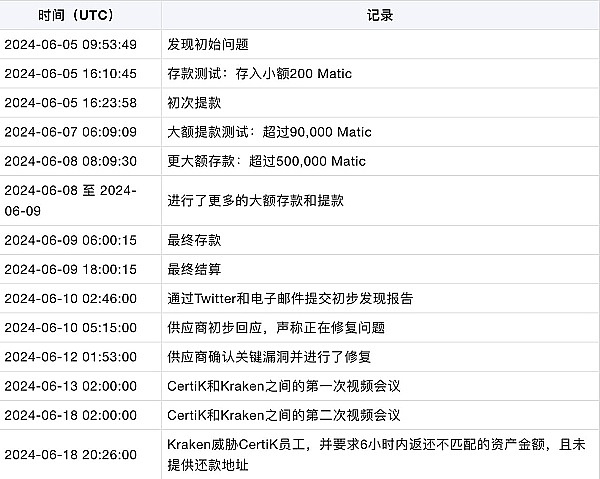
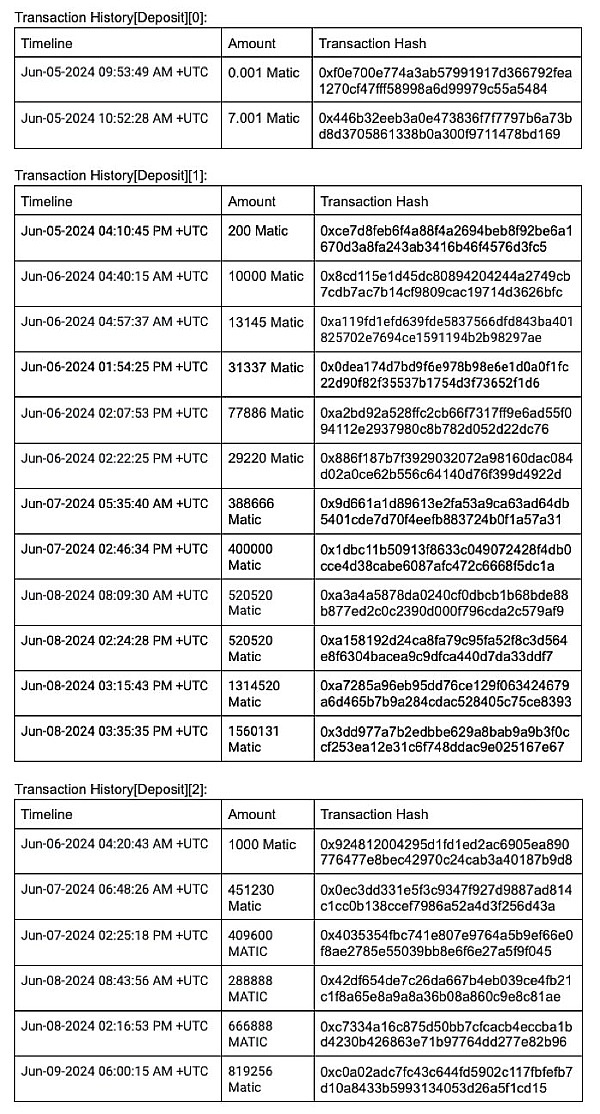
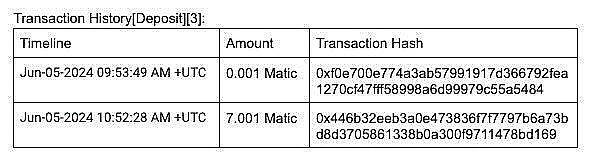
In order to allow the community to have a more transparent understanding of the full picture of the incident, CertiK provides a timeline of the incident and test deposit transaction details:
Among them, CertiK pointed out:
The facts of the white hat operation: Millions of dollars of cryptocurrency were minted out of thin air, and no real Kraken user assets were involved in the research activities.
More serious security issues: Over a period of several days, many fake tokens were generated and withdrawn as valid cryptocurrencies, and no risk control or prevention mechanism was triggered until CertiK reported it.
The real question: Why did Kraken's defense-in-depth system fail to detect so many test transactions. Continuous large withdrawals from different test accounts are part of CertiK's testing of the system's limits.
Conclusion
In the spirit of transparency and commitment to the Web3 community, CertiK chose to make this public to protect the safety of all users. CertiK urges Kraken Exchange to stop any threats to white hat hackers, work together to face risks and safeguard the future of Web3.
 JinseFinance
JinseFinance