Source: Chainalysis; Compiled by: Songxue, Golden Finance
In the past few years, cryptocurrency hacking has become a common and powerful threat, resulting in billions of dollars in cryptocurrency platforms being hacked. theft, and exposed vulnerabilities throughout the ecosystem. As we revealed in last year’s Cryptocurrency Crime Report,2022 was the worst year ever for cryptocurrency thefts, The amount stolen amounted to $3.7 billion. However, By 2023, stolen funds decreased by approximately 54.3% to $1.7 billion strong>, although the number of individual hacking incidents has actually increased, from 219 in 2022 to 231 in 2023.
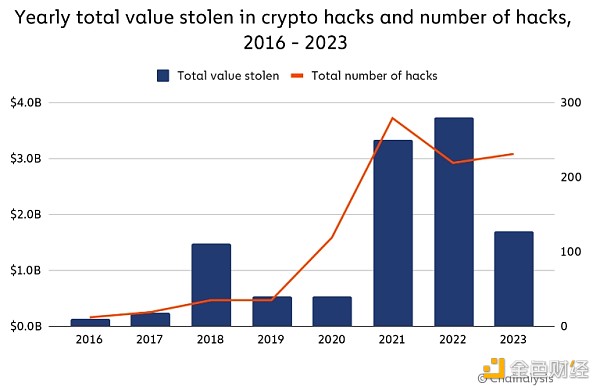
Why has the number of stolen funds dropped significantly? Mainly due to the decrease in DeFi hacking attacks. In 2021 and 2022, hacks of DeFi protocols dominated the trend of significant increases in stolen cryptocurrencies, allowing hackers to steal more than $3.1 billion from DeFi hacks in 2022. But in 2023, hackers only stole $1.1 billion from DeFi protocols. This is equivalent to a 63.7% year-on-year decrease in the total annual stolen value of DeFi platforms. The share of total stolen funds held by victims of DeFi protocols also dropped significantly in 2023, as shown in the chart below.
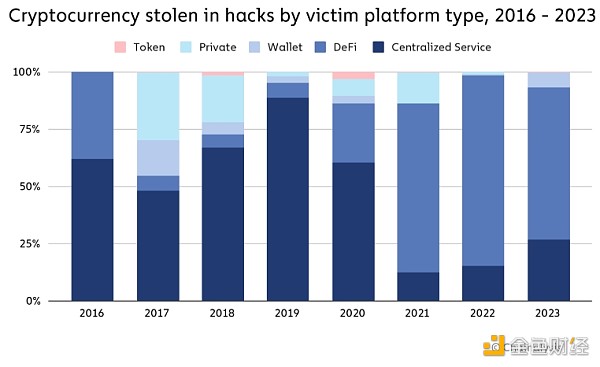
We will follow Possible reasons for the decline in DeFi hacking attacks are explored in more detail. Despite this decrease, 2023 still saw large-scale hacks of important DeFi protocols. For example, Euler Finance, a lending protocol running on Ethereum, experienced a flash loan attack in March 2023, resulting in a loss of approximately $197 million. There were 33 hacks in July 2023, the most of any month, including the theft of $73.5 million from Curve Finance. We can see the spikes driven by these attacks in the chart below.
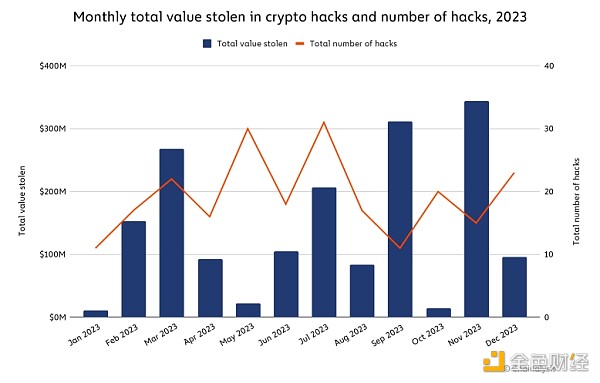
Similarly, in 2023 In September and November of this year, several large-scale attacks occurred on both DeFi and CeFi platforms: Mixin Network ($200 million), CoinEx ($43 million), Poloniex Exchange ($130 million), HTX ($113.3 million) ) and Kyber Network ($54.7 million).
North Korea-affiliated cybercriminals have had their most active year ever, executing more encryption hacks than ever before.
The attack vectors affecting DeFi are complex and diverse
DeFi hacker attacks will surge in 2021 and 2022. The attackers stole approximately $2.5 billion and $3.1 billion respectively from the protocol. Mar Gimenez-Aguilar, chief security architect and researcher at our partner Halborn, told us about the rising trend of DeFi hacking attacks in the past two years. She explained: “It is a worrying trend that the frequency and severity of attacks are escalating within the DeFi ecosystem. In our comprehensive analysis of the top 50 DeFi hacks, we observed that EVM-based chains and Solana are among the most attacked chains, primarily due to their popularity and ability to execute smart contracts." When reviewing the trend last year, security experts told us they believed many DeFi vulnerabilities stemmed from protocol operators' primary focus on Growth, rather than focusing on implementing and maintaining strong security systems.
However, for the first time since DeFi became a key sector of the crypto economy, the annual total amount stolen from DeFi protocols fell, and the decline was considerable.
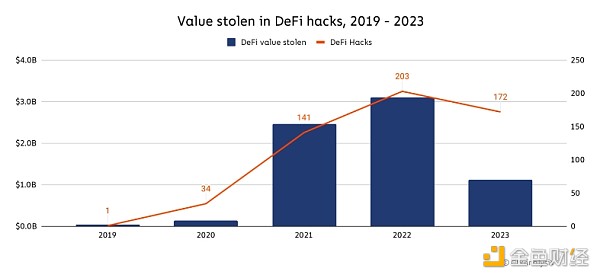
In 2023, the value caused by DeFi hacks fell by 63.7% year-on-year, and the median loss per DeFi hack dropped by 7.4%. And, while the number of individual crypto hacks rose in 2023, the number of DeFi hacks fell by 17.2%.
To better understand this trend, we teamed up with Halborn to analyze 2023 DeFi hacking activity through the lens of the specific attack vectors hackers exploited.
Classify and analyze attack vectors in the DeFi field
The attack vectors affecting DeFi are diverse and are constantly evolving; therefore, it is important to classify them to understand how attacks occur and how protocols may reduce the likelihood of their occurrence in the future. According to Halborn, DeFi attack vectors can be divided into two categories: vectors originating on-chain and vectors originating off-chain.
On-chain attack vectors do not originate from vulnerabilities in the blockchain itself, but from vulnerabilities in the on-chain components of the DeFi protocol (such as smart contracts). This is not a concern for centralized services, which do not run as decentralized applications with publicly visible code like DeFi protocols. Off-chain attack vectors originate from vulnerabilities outside the blockchain – one example might be off-chain storage of private keys in a malfunctioning cloud storage solution – and are therefore suitable for DeFi protocols and centralized services.
| Hacker attack vector subcategory | Definition | Chain On or off the chain |
| Protocol Exploitation | When an attacker exploits the protocol vulnerabilities in blockchain components, such as those related to validator nodes, the protocol’s virtual machine, or the mining layer. | on chain |
| Internal attack | When an attacker inside the protocol (such as a rogue developer) uses a privileged key or other private information when directly stealing funds. | Under the chain |
| Phishing | When an attacker tricks a user into signing for permission, it is usually by substituting a legitimate protocol. Completed, thus allowing the attacker to spend tokens on behalf of the user. Phishing can also occur when an attacker tricks a user into sending funds directly to a malicious smart contract. | Under the chain |
Diffusion
| < td width="167" valign="top" style="word-break: break-all; border-width: 1px; border-style: solid;">When an attacker creates a vulnerability due to a hack in another protocol And when using a protocol. The proliferation also includes hacks closely related to hacks in other protocols. on chain |
| Server damaged | When an attacker compromises a server owned by the protocol, thereby disrupting the normal operation of the protocol workflow or gain knowledge to further exploit the protocol. | Under the chain |
| Wallet Hacker | When an attacker exploits a protocol that provides custody/wallet services and subsequently obtains the relevant wallet When operating information. | Under the chain |
| Price manipulation hacker | When an attacker exploits a smart contract vulnerability or exploits a flawed oracle that cannot When accurate asset prices are reflected, it facilitates the manipulation of digital token prices. | on chain |
| Smart contract development | When an attacker exploits a vulnerability in the smart contract code, it is usually granted Direct access to various control mechanisms of the protocol and token transfers. | on chain |
| Private key leaked | For example, when an attacker gains access to a user's private key, this It may occur due to off-chain software leaks or glitches. | Under the chain |
| Governance attack | When an attacker gains sufficient influence or voting rights to manipulate When a blockchain project has a centralized governance structure, malicious proposals can be formulated. | on chain |
| Third party damage | < td width="167" valign="top" style="word-break: break-all; border-width: 1px; border-style: solid;">When an attacker obtains access to off-chain third-party programs used by the protocol When gaining access, the program provides information that can later be used for exploits. Under the chain |
| Other | The attack either does not fall into any of the above categories, or there is insufficient information to conduct it Correct classification. | On-chain/off-chain |
According to Gimenez-Aguilar, there are serious problems with both on-chain and off-chain vulnerabilities. “Historically, most DeFi hacks stem from vulnerabilities in smart contract design and implementation—a large proportion of the affected contracts we examined either did not undergo any auditing, or underwent insufficient auditing,” she explained There are loopholes in the chain. "Another notable trend is the increase in attacks due to private key compromise, which highlights the importance of improving security practices outside of a given blockchain."
In fact, the data It shows that the on-chain and off-chain vulnerabilities described by Gimenez-Aguilar - specifically private keys being compromised, price manipulation attacks and smart contract exploitation - all contributed to hacker losses in 2023.
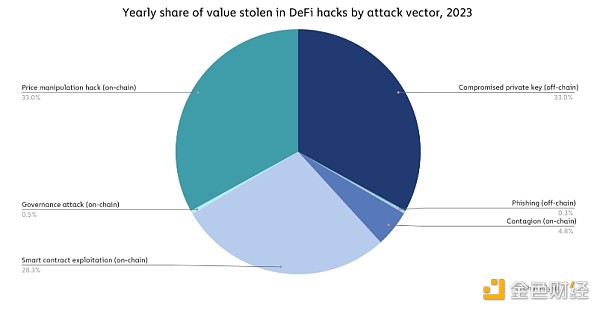
Source: Halborn
Overall, On-chain vulnerabilities fueled much of the DeFi hacking activity in 2023, but as we can see in the image below, this changed over the course of the year, with private keys compromised in The third and fourth quarters drove a greater proportion of hacking attacks.

Source: Halborn
From the perspective of successive hacking attacks, Hacks originating from proliferation (on-chain) were the most damaging, with a median loss of $1.4 million. Governance attacks (on-chain), insider attacks (off-chain), and private key compromises (off-chain) follow closely behind, with the median hack value for all three being around $1 million.
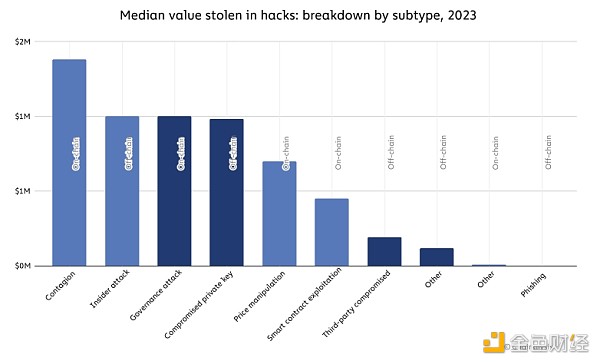
Source: Halborn
Overall, the data provides reason for optimism. The decline in raw value stolen from DeFi in 2023, and the relative decline in hacks driven by on-chain vulnerabilities during 2023, suggestDeFi operators may be improving smart contract security. “I do think the increase in security measures in DeFi protocols is a key factor in reducing the number of hacks related to smart contract vulnerabilities. If we compare this year’s top 50 hacks by value to previous hacks When comparing attacks (studied in Halborn’s Top 50 Hackers report), the percentage lost from total losses decreases from 47.0% overall to 18.2%. However, the proportion of price manipulation attacks remains almost the same at approximately 20.0% of value. This suggests that when conducting audits, protocols should also consider their interactions with the entire DeFi ecosystem,” Gimenez-Aguilar said. However, she also highlighted that the growth in hacking attacks driven by attack vectors such as compromised private keys shows that DeFi operators must look beyond smart contract security to address off-chain vulnerabilities: “Make the same comparison as before, related to compromised private keys The loss increased from 22.0% to 47.8%.” As shown above, both on-chain and off-chain vulnerabilities can be highly damaging.
However, Gimenez-Aguilar also admitted that The decline in DeFi hacking losses may be partly due to DeFi activity in 2023 The reason for the overall decrease may simply be a reduction in the number of DeFi protocols being attacked by hackers. Total value locked (TVL), which measures the total value held or staked in DeFi protocols, has been declining throughout 2023, following a sharp decline in mid-2022.
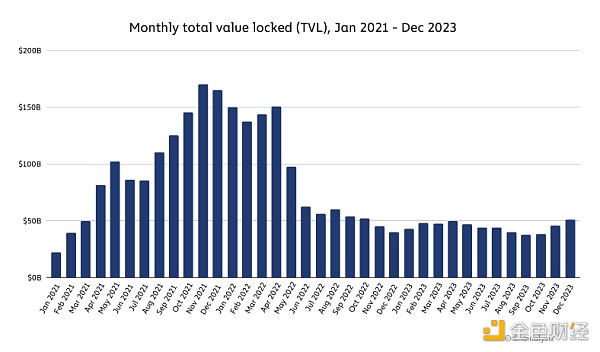
Source: DeFiLlama
We cannot be certain that the decline in DeFi hacking is primarily due to better security practices Or a decline in overall DeFi activity - most likely a mix of the two. However, if the decrease in hacking is primarily caused by a decrease in overall activity, it will be important to see whether DeFi hacking rises again with another DeFi bull run, as this will lead to a higher TVL and thus a higher level of investment for hackers. Use a larger DeFi capital pool to attack.
Regardless, DeFi operators should take steps to improve security. DeFi protocols that are vulnerable to on-chain failures could develop systems that monitor on-chain activity related to economic risk and previous platform losses. For example, companies like Hypernative and Hexagate produce customized alerts to prevent and respond to cyberattacks, which helps platforms better protect integrations with third parties like Bridges and communicate with customers who may be compromised Communicate. Platforms vulnerable to off-chain failures may strive to reduce their reliance on centralized products and services.
North Korea hacked more crypto platforms than ever before in 2023, but stole less than in 2022< /h2>
In recent years, North Korea-related hacking attacks have been on the rise, with cyber espionage groups such as Kimsuky and Lazarus Group using various malicious means to obtain large amounts of crypto assets. In 2022, cryptocurrency stolen by North Korea-linked hackers peaked at approximately $1.7 billion. In 2023, we estimate that the total amount stolen is just over $1 billion, but as we can see below, the hack The number reached 20 - the highest on record.
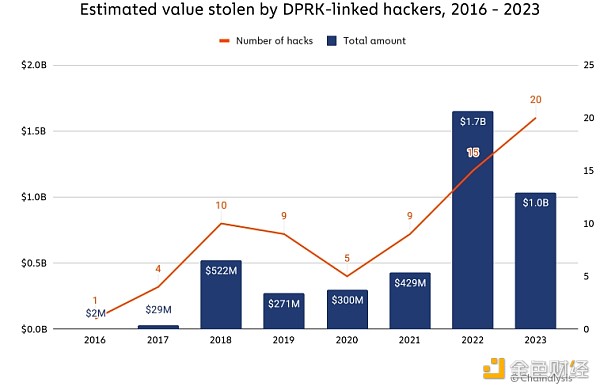
We estimate that North Korea-related hackers stole approximately $428 million from DeFi platforms in 2023, and also targeted centralized services ($150 million stolen), exchanges ($330.9 million stolen) and Wallet provider ($127 million stolen).
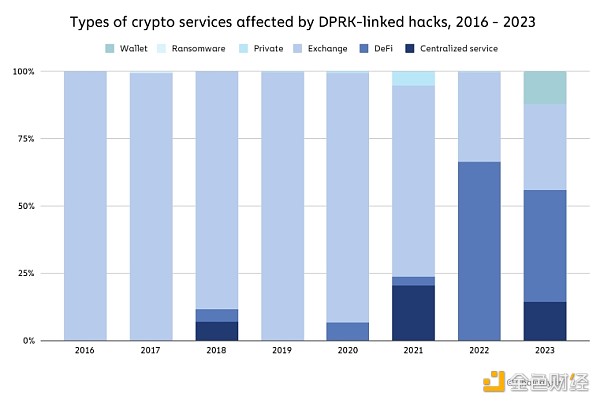
2023, North Korea There has been a significant decrease in attacks against DeFi protocols, reflecting the overall decline in DeFi hacks we discussed above.
Case Study: North Korea’s Wallet Vulnerability
In June 2023, thousands of Atomic Wallets users of , a non-custodial cryptocurrency wallet service, were targeted by hackers, resulting in an estimated loss of $129 million. The FBI later attributed the attack to the North Korea-linked hacking group TraderTraitor and said the Atomic Wallet exploit was the first in a series of similar attacks, including the Alphapo and Coinspaid attacks later that month. While the exact details of the attack remain unclear, we used on-chain analysis to see where the funds flowed after the initial attack, which we divided into four stages.
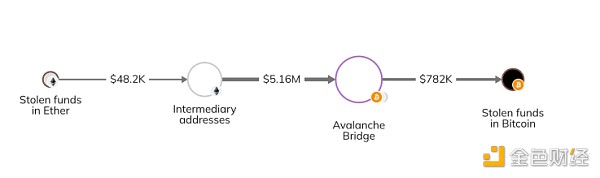
In the first stage, the attacker performed a cross-chain operation—moving assets from one blockchain to another, often to obfuscate the flow of illegally obtained funds—by moving funds through the following three methods To the Bitcoin blockchain:
Send funds to a centralized exchange . While we are unable to continue to track the on-chain movement of the funds after being transferred to a centralized service, we do know in this case that the funds stolen from the Atomic Wallet were converted to Bitcoin on the centralized exchange because we have received additional data from other regular Intelligence was gathered from cooperating trusted sources.
Send funds to the cross-chain bridge, which can then move them to the Bitcoin blockchain.
Send funds to a wrapped Ethereum (wETH) contract and then transfer to the Bitcoin blockchain via the Avalanche Bridge.
Chainalysis Reactor The third method shown below the chart is that the stolen funds (Ethereum at the time) traveled through many times before reaching the Avalanche Bridge and converting to Bitcoin. an intermediate address.
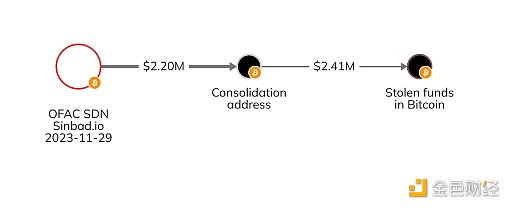
In the second stage , the attackers sent stolen funds to OFAC-sanctioned Sinbad, which provides a mixer service that can obfuscate on-chain transaction details and has previously been used by North Korean money launderers. The attackers then withdrew the funds from Sinbad and moved them to Bitcoin integration addresses.
In the third stage , the attacker’s money laundering strategy shifted almost entirely to the Tron blockchain rather than the Bitcoin blockchain. The attacker cross-chained to the Tron blockchain through one of the following methods:
Put Funds are sent to Avalanche and crossed to the Tron blockchain via the Avalanche bridge.
Send funds to a centralized service that then transfers them to the Tron blockchain.
Send funds through other mixed cryptocurrencies or privacy-enhancing services to further obfuscate the flow of funds, which are then transferred to the Tron blockchain.
In the fourth and final stage, the attacker deposits funds into various services on the Tron blockchain. Some of the funds were mixed through Tron’s JustWrapper Shielded Pool, while others ended up being sent to high-activity Tron addresses suspected of belonging to OTC traders.
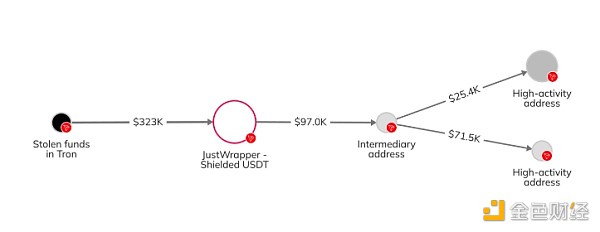
Other on-chain activity shows that funds stolen from Atomic were merged with assets from other sources before being moved elsewhere, which may be related to the subsequent Alphapo and Coinspaid breaches.
The future of cryptocurrency hacking
Although the total amount stolen from crypto platforms in 2023 is higher than in previous years Significant reduction, but attackers are becoming increasingly sophisticated and diverse in their attack methods. The good news is that crypto platforms are also becoming more sophisticated in terms of security and responding to attacks.
When crypto platforms act quickly after being attacked, law enforcement agencies will be better able to contact the exchange where the frozen funds are located to seize them, and contact the services where the funds flowed to collect relevant information about accounts and users. . As these processes continue to improve, the amount of money stolen from crypto hacks is likely to continue to decrease.
 JinseFinance
JinseFinance
















