Author: Matthew GreenTranslator: Block unicorn
About the author, Matthew Green is a cryptographer and a professor at Johns Hopkins University. I design and analyze encryption systems used in wireless networks, payment systems, and digital content protection platforms. In my research, I study the various ways that encryption technology can be used to protect user privacy.
This article was inspired by the recent worrying news that Telegram CEO Pavel Durov was arrested by French authorities for failing to adequately regulate content. While I don't know the specifics, using criminal charges to coerce social media companies is a rather worrying escalation, and things don't seem as simple as they seem.
But I don't want to talk about this arrest today.
I want to talk about one specific detail in the reporting, specifically: Almost every news report about the arrests referred to Telegram as an “encrypted app.” Here are a few examples:
This statement drives me crazy because, from a very limited technical perspective, it’s not wrong. However, on every important level, it fundamentally misleads people about Telegram and how it actually works. This misrepresentation is bad for journalists and Telegram’s users, especially those who could be seriously harmed by it.
Now let’s get to the details.
Is Telegram encrypted?
Many systems use encryption in some way, however, when we talk about encryption in the context of modern private messaging services, the word usually has a very specific meaning: It refers to the use of default end-to-end encryption to protect the contents of a user's messages. When used in an industry-standard way, this feature ensures that each message is encrypted using an encryption key that is known only to the two parties communicating, and not to the service operator.
From your perspective as a user, an "encrypted messaging app" means that every time you start a conversation, your messages can only be read by the person you're chatting with. If the operator of the messaging service tries to view the contents of your messages, all they'll see is useless encrypted data. The same assurances apply to anyone who might hack into the provider's servers, as well as to law enforcement agencies that serve the provider a subpoena, for better or for worse.
Telegram clearly doesn’t fit this stricter definition, and for one simple reason:It doesn’t have end-to-end encryption enabled by default. If you want to use end-to-end encryption in Telegram, you have to manually activate an optional end-to-end encryption feature called “Encrypted Chat” for each private conversation. This feature is explicitly not enabled for most conversations, and only works for one-on-one conversations, never for group chats of more than two people.
As a weird “add-on,” actually activating Telegram’s end-to-end encryption is a pain for non-expert users.
First, the button that activates Telegram’s encryption feature isn’t visible in the main conversation window or on the home screen. To find it in the iOS app, I had to tap it at least four times—once to go to the user’s profile page, once to have a hidden menu pop up to reveal the option, and finally to confirm that I wanted to use encryption. And even then, I couldn’t actually start an encrypted conversation, because the “Encrypted Chat” feature only works if the person you’re talking to happens to be online.
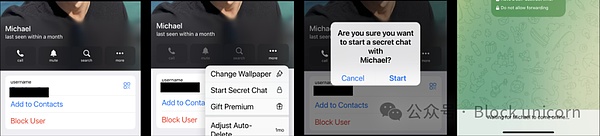
Starting an "encrypted chat" with my friend Michael in the latest Telegram iOS app, this option is not directly visible from the normal chat interface. Activating it requires four taps:
(1) Going to Michael's profile page (left image),
(2) tapping the "..." button to reveal a hidden set of options (center image),
(3) selecting "Start secret chat",
(4) tapping OK in the "Are you sure you want to continue" confirmation dialog. Afterwards, I still couldn't send Michael any messages,
because Telegram's secret chat feature is only enabled when the other person is also online.
Overall, this is a very different experience than starting a new encrypted chat in a modern industry-standard encrypted messaging app, where you just open a new chat window.
While this may seem like nitpicking, the difference between end-to-end encryption by default and this experience can be quite significant. In practice, this means that the vast majority of one-on-one Telegram conversations — and every single group chat — are potentially visible and logable to Telegram’s servers, which can see and log the contents of all messages sent between users. This may or may not be a problem for every Telegram user, but it’s clearly not something that should be promoted as particularly securely encrypted.
(If you’re interested in the details, as well as some further criticisms of Telegram’s actual encryption protocol, I go into that further below.)
Does Encryption by Default Really Matter?
Maybe, and maybe not! There are two different ways to look at this question.
One angle is that Telegram's lack of default encryption is totally fine for a lot of people. The reality is that a lot of users simply don't use Telegram as an encrypted private messaging tool. For many people, Telegram feels more like a social media network than a private messaging app.
Specifically, Telegram has two popular features that make it a good fit for this use case. One is the ability to create and subscribe to "channels," each of which is like a broadcast network where one person (or a handful of people) can push content to millions of readers. When you're broadcasting messages to thousands of strangers, keeping the contents of your chat private isn't as important.
Telegram also supports large public group chats with thousands of users. These groups can be open to the public or set to invite-only. While I personally have never thought about sharing a group chat with thousands of people, I've heard that many people like this feature. In such large, public groups, the unencrypted nature of Telegram group chats doesn’t really matter that much — after all, who cares about encryption when you’re talking in a public square?
But Telegram isn’t limited to these features, and many users who join these features do other things, too.
Imagine you’re in a large group chat in a “public square.” In this setting, there’s probably no expectation of strong privacy, so end-to-end encryption isn’t important to you. But suppose you and five friends leave the square to have a private conversation. Does that conversation deserve strong privacy? It doesn’t matter, because Telegram doesn’t offer that protection, at least in the default encryption, which doesn’t protect you from content being shared with Telegram’s servers.
Similarly, suppose you use Telegram’s social media features, primarily to consume content rather than to generate it. But one day your friend, who also uses Telegram for similar reasons, sees you on the platform and decides to send you a private message. Are you concerned about privacy now? Do you manually turn on the "encrypted chat" feature - even though it requires four explicit clicks through a hidden menu and will prevent you from communicating immediately if one of you is offline?
I strongly suspect that many people who may have joined Telegram for its social media features will also end up using it for private chats. I think Telegram knows this and tends to promote itself as a "secure messaging app" and talk about the encryption features of the platform precisely because they know it will make people feel more comfortable. But in reality, I also suspect that few of these users are actually using Telegram's encryption features. Many users may not even know that they need to manually turn on encryption and may think they are already using it.
This leads me to my next point.
Telegram knows its encryption is difficult to turn on, but continues to promote its product as a secure messaging app
Telegram’s encryption has been heavily criticized since 2016 (and probably earlier) for many of the reasons I mentioned in this post. In fact, many of these criticisms were made by experts, including me, in conversations with Pavel Durov on Twitter many years ago.
Despite the sometimes scathing interactions with Durov, at that time I still mostly believed that Telegram had good intentions. I assumed that Telegram was busy expanding its network, and that over time they would improve the quality and usability of the platform’s end-to-end encryption: for example, by making it the default, supporting group chats, and making it possible to start encrypted chats with offline users. I assumed that while Telegram might be a follower rather than a leader, it would eventually reach a level of functionality on the encryption protocol comparable to Signal and WhatsApp. Of course, another possibility is that Telegram will abandon encryption altogether and focus on being a social media platform.
What actually happened is even more confusing to me.
Telegram’s owners have done nothing to improve the usability of its end-to-end encryption, and its encrypted user experience has barely changed since 2016. Despite some upgrades to the underlying encryption algorithms used by the platform, the user experience of secret chats in 2024 is virtually indistinguishable from that of eight years ago. Despite this, the number of Telegram users has grown seven to nine times over the same period.
Meanwhile, Telegram CEO Pavel Durov continues to actively promote Telegram as a “secure messaging app.” Recently, he delivered a pointed critique of Signal and WhatsApp on his personal Telegram channel, implying that these systems are backdoored by the US government and that only Telegram’s independent encryption protocol is truly trustworthy.
If this were a legitimate technical argument between two platforms that both support end-to-end encryption by default, this might be understandable. However, Telegram really has no place in this discussion. It’s no longer interesting to see the Telegram organization encouraging users to move away from messaging apps that are encrypted by default, while refusing to implement basic features that would widely encrypt user messages. In fact, it’s starting to look a bit malicious.
What else are the encryption details?
This is a cryptography blog, so I’d be remiss if I didn’t spend a little time talking about boring cryptographic protocols. I’d also miss a great opportunity to marvel at the internal details of Telegram’s encryption, which almost always leave me dumbstruck every time I look at them.
To save myself the pain, I’ll cover these details in a paragraph, so feel free to skip if you’re not interested.
Telegram's secret chat feature is based on a custom protocol called MTProto 2.0, according to what I believe to be the latest cryptographic specifications. This system uses a 2048-bit finite field Diffie-Hellman key exchange, with group parameters (I think) chosen by the server. (Since Diffie-Hellman key exchange requires both users to be online, an encrypted chat cannot be set up if one user is offline) MITM protection is handled by the end user, who must compare key fingerprints. The server provides some weird random nonces (random values) that I don't fully understand the purpose of* - these used to make key exchange completely insecure against malicious servers in the past (but this problem has long been solved*). The generated keys are then used in the most amazing, non-standard authenticated encryption mode - a mode called "Infinite Obfuscation Extension" (IGE), which is based on AES and uses SHA2 to handle authentication. **
Note: In the paragraph above, every place I marked with a "*" is a point that an expert cryptographer would raise their hand and ask in the context of something like a professional security audit. I'm not going to go into detail, suffice it to say, Telegram encryption is very unusual.
If you asked me to guess whether the protocol and implementation of Telegram secret chats are secure, I would say it's probably secure.Honestly, but it doesn't matter because it doesn't matter if people don't actually use it.
Block unicorn note: In short, Telegram's encryption system uses some complex technology to protect information, but in terms of user experience, it's complicated to set up and use. Some of the technical details can feel a bit opaque, especially the use of random numbers and how the keys are protected.
Finally
While end-to-end encryption is one of the best tools we have developed to prevent data breaches, it’s not the whole story. One of the biggest privacy issues in messaging is the large amount of metadata — basically data about who is using the service, who they are talking to, and when they are talking.
This data is not usually protected by end-to-end encryption. Even in apps that only have a broadcasting function, like Telegram’s channels, there is a lot of useful metadata about who is listening to the broadcast. This information itself is valuable to people, as can be seen by the huge amounts of money that traditional broadcasters spend to collect this data. At present, all of this information is probably sitting on Telegram’s servers, accessible to anyone who wants to collect it.
I’m not criticizing Telegram specifically, as the same issues exist for almost every other social media network and private messaging app. It should be mentioned, but I mention these issues to avoid giving you the impression that just having encryption is enough.
 JinseFinance
JinseFinance






