According to DefiLlama reports, the cumulative funds stolen from cross-chain bridges so far have exceeded US$2.8 billion, accounting for almost 40% of the total stolen funds in the entire Web3 industry.
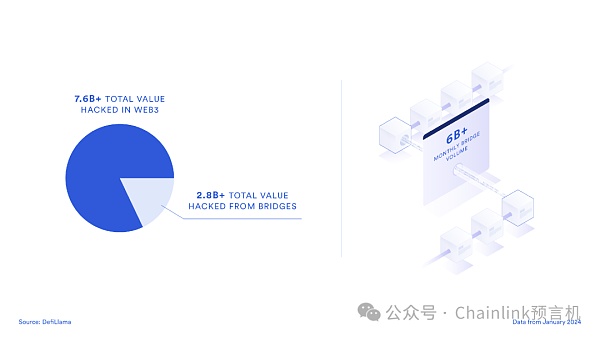
The total amount of stolen funds in the entire Web3 industry is US$7.68 billion, of which US$2.83 billion was stolen from cross-chain bridges, making it one of the most severely attacked tracks
There is no doubt that cross-chain is a key element to stimulate Web3 innovation. However, it also creates potential attack vectors. In the software industry, many developers believe in the principle of "move fast and break things." But once it comes to the cross-chain security of tens of billions or even trillions of dollars of user funds, this principle is completely unworkable. If you go too fast, things can go wrong.
What is a cross-chain bridge?
Cross-chain bridge is a decentralized application that can transfer assets from one blockchain to another.
Today, cross-chain bridges vary widely in design and purpose. For example, some cross-chain bridges are specifically designed to transfer funds between L2 and the underlying blockchain. The universal cross-chain bridge developed based on cross-chain protocols such as Chainlink CCIP can seamlessly transmit assets and messages between various blockchains.
Cross-chain bridge is the core element of Web3 infrastructure. For users, cross-chain bridges can seamlessly transfer tokens and messages between chains; for developers, cross-chain protocols can be used to create a user experience that is compatible with any blockchain, which greatly Simplify infrastructure. Today, the monthly transaction volume of all cross-chain bridges totals more than 6 billion. Obviously, this track has become an indispensable part of the Web3 ecosystem and has been widely used.
Therefore, whether you are a user, developer or institution, if you want to study the cross-chain track, you mustunderstand the seven keys of cross-chain bridges vulnerabilitiesto protect themselves, their users, and their stakeholders.
Private Key Management Vulnerability
Cross Chain bridges are usually managed using one or a set of private keys. One or more cross-chain bridge running nodes will each hold a unique private key. Their task is to reach a consensus on the value of cross-chain messages or transfers sent by users, and to accurately transmit the messages or values across chains. They will use private keys to digitally sign, or use multiple private keys to form threshold signatures to approve cross-chain messages.
Therefore, private key theft is one of the most common vulnerabilities of cross-chain bridges. The most notorious cross-chain bridge theft incident in the Web3 industry was caused by the theft of private keys. Theft of private keys is usually due to vulnerabilities in private key management or cross-chain bridge operation security.
A general principle is that if the cross-chain bridge and its private key are in the server, infrastructure provider, deployment location and node operator, The more decentralized it is, the more capable it is of preventing single points of failure and centralization risks.
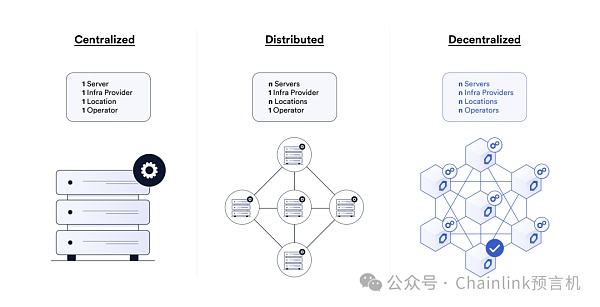
Centralized networks are not only vulnerable to attacks, but also situations where one party has full control over all user funds
The decentralized model can be effective Prevent the risk of centralization. In decentralized mode, any attacker (or even a node running a cross-chain bridge) must attack the private keys of multiple independent entities at the same time to be successful, thus greatly reducing the probability of internal and external attacks. . This is a very robust security model. However, there are other factors that need to be considered to keep private keys safe. Another equally important factor is that each cross-chain bridge operating node needs to independently adopt different security mechanisms to ensure the security of private keys.
Best Practices
While decentralization can be It is best to avoid single points of failure, but to ensure the security of private keys, multiple measures need to be taken at the same time. The most secure cross-chain protocols usually use a decentralized model to ensure security and mature solutions to save private keys, such as hardware security modules (HSM), encryption (data in transit and data at rest) , Internet fraud prevention education, authority control and key management services, etc.
Real case of cross-chain bridge being attacked due to stolen private key
Ronin Cross-Chain Bridge (March 2022)——In Ronin Five of the nine private keys required to conduct, approve and execute transactions on the cross-chain bridge were stolen.
Harmony Cross-Chain Bridge (June 2022)——In Harmony Cross-Chain Bridge Two of the five private keys needed to conduct, approve and execute transactions on the Internet were stolen.
Multichain cross-chain bridge (July 2023)——Cross-chain bridge The private key was stolen, resulting in funds being withdrawn without approval. These private keys are held by the CEO of Multichain.
Orbit Chain (January 2024)——Ten private keys of Orbit Chain cross-chain bridge Seven of the keys were stolen, causing the fund pool to be drained.
Smart contract audit vulnerability
Since the main function of a cross-chain bridge is to transfer value from one chain to another, all cross-chain protocols must involve smart contracts.
In most cross-chain use cases, smart contracts on multiple chains need to be used to mint, destroy, lock or unlock cross-chain tokens. These smart contracts are connected through cross-chain bridges, often in partnership with token issuers.
It can be said that smart contracts are an extra layer of security to prevent cross-chain bridge theft, but if there are loopholes in the smart contract itself, it may also lead to technical risks. On the one hand, smart contracts provide a valuable platform for cross-chain bridges to carry out various routine security checks, such as ensuring that the amount withdrawn by users does not exceed the amount deposited and setting a rate limit for cross-chain bridges. On the other hand, if the smart contract code is of poor quality or has not been rigorously audited, it will be counterproductive. Hackers have stolen huge amounts of funds from multiple cross-chain bridges by exploiting vulnerabilities in smart contract code.
No project, no matter how much it values security, cannot completely guarantee that there are no technical vulnerabilities in its smart contract code. However, there is a very mature solution that can ensure the robustness of the code, which is to cooperate with an experienced third-party auditor to test the project code base and release it after passing the test. This is not a one-and-done thing, as even the most complete codebase can immediately revert to an unaudited state once changes are made to the codebase after an audit, or if unaudited smart contracts are added to an audited codebase.
Best Practices
When using cross-chain protocols , the risks of smart contracts are real. The most secure cross-chain bridges tend to have multiple ongoing internal audits and competitive external audits of their code bases. In addition, these cross-chain bridges will also conduct a series of internal security tests, such as fuzz testing, static analysis, formal verification, and symbolic execution.
If you want to understand the potential technical risks of a cross-chain bridge, you need to check the number of audits of its code base and the auditors and other related information. In addition, it is also necessary to establish multi-layer security models such as emergency shutdown and emergency updates, and set rate limits, which can effectively reduce the risk of smart contract vulnerabilities.
A real case of cross-chain bridge theft due to smart contract vulnerabilities
Wormhole cross-chain bridge (February 2022) -Hacker found A vulnerability in the verification step of the cross-chain bridge smart contract resulted in 120,000 wETH being minted on the Solana chain without sufficient collateral assets.
Nomad cross-chain bridge (August 2022)——Cross-chain bridge smart contract There is an error in the implementation of the root account (0x00) that is accepted by default in the code, allowing anyone to steal funds from the cross-chain bridge.
Binance Cross-Chain Bridge (October 2022)——Cross-chain Bridge Intelligence In the contract, IAVL Merkel proved that there was a vulnerability in the verification system, resulting in the cross-chain bridge being attacked. The attack caused 2 million BNB to be transferred from the cross-chain bridge to the attacker's account.
Socket Interoperability Protocol (January 2024) - The protocol smart contract has a vulnerability, This causes the wallet to have unlimited approvals for the Socket smart contract.
Upgrade process vulnerability
Upgradeability refers to the ability to upgrade the smart contract code, or the ability to change some parameter configurations in the smart contract code.
Developers typically adopt upgradable smart contracts for upgrades to add new features, resolve smart contract logic errors, and modify key risk parameters. Cross-chain bridges can be upgraded to add new tokens and blockchains, adopt new technologies to verify cross-chain messages, adjust key risk parameters such as fund withdrawal limits and node composition, and quickly resolve any newly discovered logic in the underlying smart contracts mistake.
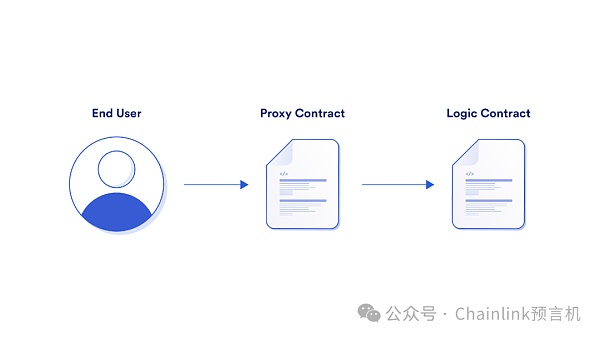
Upgradable smart contracts require the development of proxy contracts between end users, front-end implementations, and underlying smart contracts
Upgradability is important for security This is critical because if there is a vulnerability in the upgrade process, it could create a potential attack vector. For cross-chain bridges to be securely upgradable, they need to adopt a defense-in-depth mechanism, including establishing a robust private key management mechanism, with keys held by multiple independent entities; using a time lock delay mechanism to allow users to Check the changes in advance before they take effect; establish a robust approval process. For example, cross-chain bridge running nodes can veto decisions within the time lock validity period with one vote. In special cases, if an upgrade needs to be implemented quickly, the cross-chain bridge running node can directly approve the change after evaluating the change resolution.
Best Practices
Continuously adapt to developments To need and cope with unknown situations, scalability must be achieved. However, if there are loopholes in the upgrade process, it may bring potential risks to the cross-chain protocol. Time-lock smart contracts and node one-vote veto mechanisms are important tools that can strengthen the upgrade process. However, to ensure the safety of cross-chain bridges, emergency plans must be developed while ensuring the highest level of security.
Reliance on a single network
Some cross-chain bridges Rely on a single validator network for all cross-chain operations. If the cross-chain bridge is specifically designed to connect two designated blockchains, then a single network solution may be feasible. But if you want to use a universal cross-chain bridge to connect the multi-chain world, then this solution is neither safe nor scalable.
There is one most important reason to avoid using this type of cross-chain bridge, and that is that once the cross-chain bridge is attacked, users will be hit hardest. Since all cross-chain transactions and their value are supported by a network, once the network is successfully compromised, all cross-chain bridges of the blockchain will be wiped out, making the risk almost impossible to isolate.
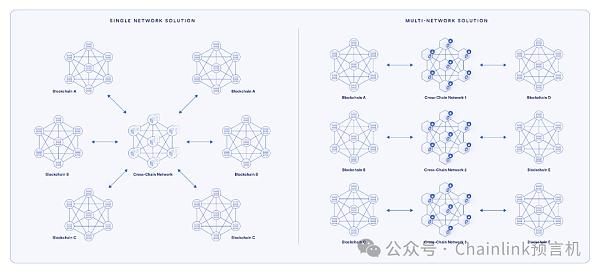
Using multiple independent decentralized networks can effectively isolate risks and prevent all blockchain and user funds from being stolen due to a cross-chain bridge attack
Using an independent multi-network design structure is a more secure and scalable solution, as follows:
Cross-chain channels are run by independent decentralized networks. This means that each cross-chain channel has an independent decentralized network, and there is a separate cross-chain channel between every two blockchains. This can limit the impact of an attack to a certain cross-chain channel.
Each cross-chain channel is secured by multiple networks. The most secure cross-chain bridges and protocols create multiple networks for each cross-chain channel to enhance security. In this way, an attacker must compromise multiple networks of a secure channel at the same time to succeed. Therefore, this also provides an additional layer of security to the secure channel.
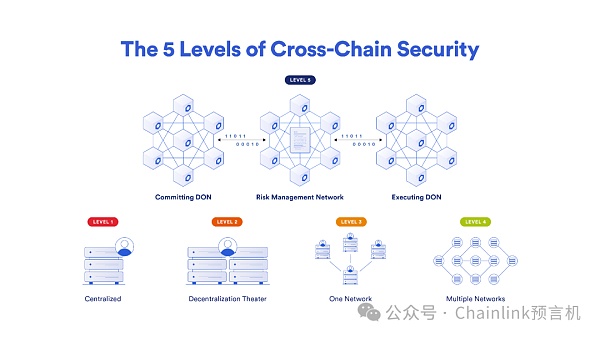
Chainlink CCIP establishes multiple networks for a single cross-chain channel and is the only cross-chain protocol that reaches the fifth (and highest) layer of cross-chain security
Best Practice
Create multiple independent channels for each cross-chain channel A centralized network can significantly reduce the attack surface and the attacker's rate of return. Best practices for this solution also include using multiple programming languages to develop clients to achieve client diversity; creating separate node collections to ensure that these nodes do not overlap with network nodes; and adding active risk control functions.
The quality of the verification node set is poor
The verification node is all The soul across the Chain Bridge. Nodes include various types of people and organizations, who are responsible for maintaining infrastructure and running cross-chain bridge functions.
Users, institutions, and dApp developers should be alert to the risk of validators being unable to safely operate cross-chain bridges due to lack of experience and knowledge. The most secure cross-chain bridges usually require their verification nodes to have world-class levels and rich experience, ensure operational security (OPSEC), keep private keys properly and reliably process and execute cross-chain transactions.
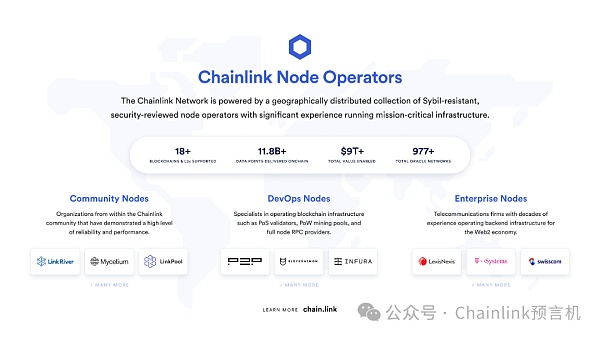
Chainlink nodes and oracle networks are run by world-class node operators
The second point is often cited by users, developers and ignored by the organization. For any cross-chain bridge user, the biggest risk in the node network is the inability to reliably execute transactions. For example, a user locks funds on one chain and then prepares to mint corresponding funds on another chain. But if minting cannot be approved because the node network is offline, user funds are effectively frozen.
Best Practices
Cross-chain bridges should only be used High-quality nodes, and these nodes must have rich operational security experience, excellent performance and strong robustness. Operational security is not a unique capability of Web3, so many Web2 and Web3 verification nodes can join. However, it is necessary to verify the node’s past record when recruiting cross-chain bridge nodes. In addition, the verification node can also be required to pledge. Once there is any violation or operation, the pledged deposit will be confiscated. Doing so incentivizes validators to work honestly and reliably and creates a new layer of economic security.
Lack of active transaction monitoring
Active monitoring of transactions The purpose is to monitor the abnormal behavior of the cross-chain bridge in real time and respond. If the active transaction monitoring mechanism is implemented properly, suspicious behavior can be well detected and necessary defensive measures can be taken immediately to prevent attacks.
A typical use case for active transaction monitoring is the emergency shutdown of cross-chain systems before executing suspicious transactions or after passing malicious transactions. Malicious transactions include successfully withdrawing all assets across a cross-chain bridge when there are insufficient collateral assets.
Real case of cross-chain bridge theft due to lack of active transaction monitoring
Ronin Cross-Chain Bridge (March 2022)— — According to Halborn blockchain security company, the Ronin cross-chain bridge was stolen six days before it was discovered. If Ronin had established a proactive transaction monitoring mechanism, this problem could have been discovered and resolved in time.
Best Practices
Active transaction monitoring usually consists of a set of independent entities or node networks that are completely unrelated to the cross-chain bridge master node. Doing so provides a clear division of responsibilities and enables checks and balances to reduce the likelihood of one or a group of nodes manipulating real-time responses.
Lack of rate limit
Rate limit It's not a new concept. In the traditional software industry, rate limiting is a security mechanism used by websites to prevent DoS attacks. Data providers will also use this mechanism to prevent server downtime caused by too many API requests.
The concept is very simple: limit the number of requests in terms of time and quantity. So what kind of request is it? In the cross-chain world, rate limiting refers to limiting themaximum value of funds that can be transferred between two chains within a certain period of time.
Although this security mechanism looks simple, it is the last solid line of defense for cross-chain bridges. Even if a hacker successfully penetrates all other lines of defense, rate limiting can limit the amount they can steal from a cross-chain bridge.

Rate limiting is like punching a small hole in a bucket. Only a certain amount of water can flow out per unit time
Because A real case of cross-chain bridge theft due to lack of rate limiting
Best Practices
Rate limits for each cross-chain channel should be customized to maximize security and modularity. In addition, each cross-chain channel should also limit the total cross-chain transfer of all assets combined. Setting a reasonable throughput rate (ie: a maximum of X tokens transferred every ten minutes) can effectively prevent attackers from draining all assets in the asset pool in one transaction. In addition, you can also set a "refill rate" for each cross-chain asset and cross-chain channel to prevent attackers from waiting until the rate limit reaches zero before stealing the upper limit assets.
Chainlink CCIP can achieve it
Unprecedented cross-chain security
We must understand one thing, that is, to achieve cross-chain security, it is not enough to adopt a certain security mechanism of. In fact, to establish a robust cross-chain security model, it is necessary to adopt a defense-in-depth mechanism and comprehensively use multiple security mechanisms to comprehensively prevent attacks.
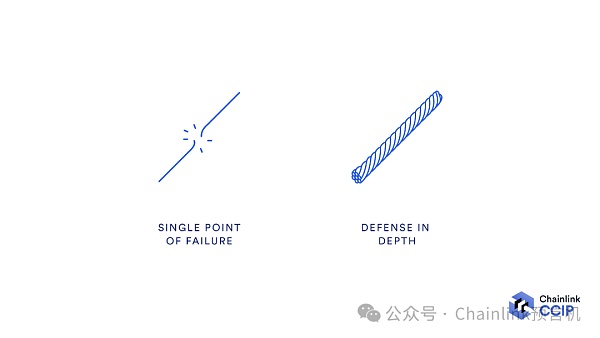
The most secure cross-chain bridges usually adopt a defense-in-depth mechanism and use a combination of multiple security mechanisms.
This is also our original intention to build the industry-standard cross-chain solution Chainlink CCIP.
 XingChi
XingChi
 XingChi
XingChi JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance cryptopotato
cryptopotato Beincrypto
Beincrypto Numen Cyber Labs
Numen Cyber Labs Cointelegraph
Cointelegraph Ftftx
Ftftx 链向资讯
链向资讯