Author: Bitrace
Introduction
This This paper was completed by Bitrace, a blockchain data analysis company from China, and ChainArgos, a blockchain intelligence company from Singapore. We conducted this paper based on the address disclosed in the judgment of the U.S. District Court of Florida in a cryptocurrency slaughter case. Digging deeper, they uncovered a large, long-standing and still active transnational fraud ring. This article aims to disclose this research result and try to alert the industry and government departments that we need to invest more attention in the field of cryptocurrency anti-fraud.
1 Introduction
Internet fraud is raging around the world like a huge epidemic, with dozens of countries losing at least tens of billions of dollars (4). A type of crypto scam called "pig-killing disk" is growing rapidly. This scam usually uses cryptocurrency as a tool to defraud the victim of funds and then clean it on the chain. (6) In this article, we will explore the use of cryptocurrencies in pig-killing scams based on victims in the People’s Republic of China and the United States of America, and demonstrate significant similarities behind cases that seemed unrelated in advance.
*The "pig-killing" scam is a trust scam and investment fraud. Victims are gradually induced to invest more and more money in seemingly legitimate cryptocurrencies before the party they are dealing with disappears.
This article will list the encryption shared by scammers in these two countries through - Currency address, using the same address for money laundering services, etc., infer that they are likely to be the same gang; from the source of the victim and the fraud wallet address indicated in the case report, trace the fraud money through the tracking system on the cryptocurrency chain to prove that there is connections; finally, through a combination of on-chain and literature research, a series of exchanges and other service providers are identified to demonstrate the current status of criminals using cryptocurrencies to commit cross-border crimes and highlight the role of global law enforcement agencies in involving such Challenges faced when scamming.
1.1 Notes on reports and documents
In order to facilitate discussion and provide reference value, all the Wallet address details. We encourage interested parties to examine and copy this work, although we understand that the vast majority of readers will not be interested in this detail.
This is not an attempt to confuse, or otherwise cause readers to check our conclusions becomes difficult. Instead, it ensures that all flowcharts are readable and that all long strings required to examine them can be easily copied from the document. The appendix contains the data needed to validate the conclusions of this article.
Furthermore, for the conclusion of this article, we have surfaced all submissions Evaluate, give equal weight between them and consider the information they contain to be reliable. It is important to note that this analysis is not intended to compare the two countries’ legal systems or police procedures, but rather to demonstrate that there are significant overlaps and similarities between the scams active in China and the United States.
2 victims
Here we explore 4 different types of victims:
A case in Florida: Florida case
< /li>A case involving victims in California and Florida: California Case
Two cases from China: China Case
*This case was brought by a court in Florida jurisdictional reasons, although victims in California lost more money. This name was chosen to reduce confusion.
The Florida case is much larger than the others and one of the victims The victim was defrauded of more than $2 million. In this case, criminals used a variety of money laundering techniques to launder the funds involved. The remaining cases were of smaller value and used fewer fund laundering methods.
2.1 Florida victims
In the Florida case, the victim fell into one of the more common pig-killing scams, court documents The description is as follows:
On April 15, 2022, Plaintiff and Defendant communicated through Facebook, an online socialmediaandsocialnetworkingservice.Id.¶10.Defendantrepresentedthatshewas successfully engaged in investing in cryptocurrency and that her aunt was a prosperous cryptocurrency trading expert who managed an analyst group at Grayscale Investments,a legitimate third-party digital currency asset management company.Id.¶¶ 11, 12. Defendant represented that, if Plaintiff were to join a margin trading platform called foundrypro.net (“Foundrypro”), Defendant would use sophisticated algorithms designed and implemented by Defendant's aunt to execute cryptocurrency trades in order to earn Plaintiff a profit. Id.¶ 13.Neither Defendant nor Defendant's aunt had a relationship with Grayscale Investments.Id.¶ 15.
Based on these representations, Plaintiff joined Foundrypro on May 17, 2022 and began executing margintradesonthatplatformonDefendant'sadvice.Id.¶ 17,19.Over the course of Plaintiff and Defendant's relationship, Plaintiff invested 2,215,118 units of “Tether”( USDT), a form of cryptocurrency known as table coin that is pegged to the value of the U.S. Dollar. Id. investment gains which, together with Defendant's representations, encouraged Plaintiff to continue “investing” in Foundrypro.(1)
After a series of judicial processes, the victim obtained a default judgment.
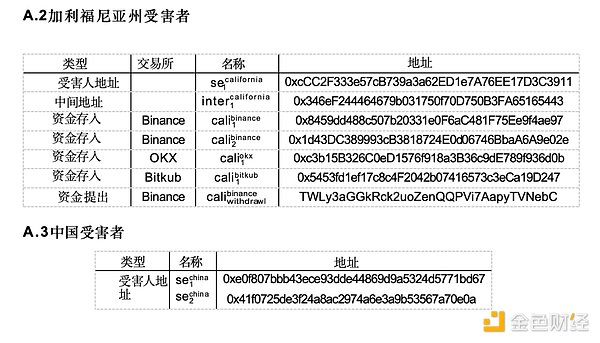
The documents in this case provide two types of cryptocurrency addresses. First, the file lists the address to which the victim initially transferred funds, which we will refer to as the victim address. Second, the document provides a list of cryptocurrency exchange deposit addresses to which victims’ funds were sent. See Appendix A.1 for details.
*Cryptocurrency exchanges offer 'deposit addresses' to simplify deposits for customers process. When a customer intends to deposit funds, the exchange creates a dedicated address for them to which they can send funds. This way, the exchange can automatically assign all transfers to that address to a specific customer account. Think of "Deposit Address" as a tool to ensure funds are sent to the correct internal account by using different external account numbers.
2.2 California Victims< /h4>
In the California case, two different people fell victim to a pig-killing scam, They sent cryptocurrency to the same scam wallet provided in Appendix A.2.
The first scam involved approximately $177,502.29 and was described in court documents as follows:< /span>
[Victim] met an individual known to him as “Bunny” through social media ( Facebook) and started a romantic relationship with her. During the relationship, Bunny offered [Victim] a way to make money through cryptocurrency so they could afford to buy a farm and live together one day.
During the relationship, Bunny convinced [Victim] to invest in cryptocurrency through “Pearcoin,” fakecryptocurrencytradingapplication,unknownto[Victim]atthetime.
Ultimately, [Victim] attempted to withdraw his funds from Pearcoin and was told he mustpaythetaxesupfrontorhewouldriska3percentpenaltyfeeforeachdayhe did not pay.At this point, [Victim] realized he was involved in a scam and subsequently contacted theBrvardCountySheriff'sOffice to report the incident.[Victim]wasunable totransfer,withdraw,oraccessanyofhisfundsthroughtheinvestmentplatform.(3)
The second scam was similar and involved approximately $300,000:
The victim ... reported she had been romantically involved with an individual through social media. During the relationship, she was convinced to invest in cryptocurrency . (3)
2.3 Chinese Victims< /span>
Bitrace provides information and data about the Chinese case. One victim from Tianjin said he was induced to open an account at the cryptocurrency exchange OKX and withdraw USDT to the trading applications WBF and Bisheng. After several smaller investments, the Tianjin victim received a return of $4,860, followed by more investments and ultimately lost approximately $40,000. There were no reports of emotional fraud in this scam, more like the butcher plate scam in the Florida case. The source of funds for the Tianjin victim se.china is in Appendix A.3, which is a wallet related to a known scam, which we will elaborate on later.
Another victim active in the OTC market reported a case involving se. china phishing scam. Phishing scams occur when victims are persuaded to download malicious "Trojan" software that empties wallets and sends funds to scammers (7;5;9). The scam appears to be linked to a smaller group than the Tianjin victims, although two of the victims Bitrace has contacted were clients of cryptocurrency exchanges who encountered the scam.
China does not have court documents like those in the United States, but we can extract local documents on similar reports of the case to further highlight such scams. Local authorities in Ningbo (2) and Wenzhou (8) reported similar scams. For example, a press release from the Wenzhou Law Enforcement Department described a scam involving "Trojan horse" software, similar to one reported by one of Bitrace's customers:
After investigation, since February 2022, the group has published advertisements selling discounted gas cards on multiple overseas social software to detect virtual currency wallets and virtual currency wallets. The authenticity of the currency is used as a guise to trick the victim into clicking on the Trojan program link and secretly control his wallet. When the time is right, he illegally obtains the virtual currency in the wallet. In just one month, he committed more than 30 crimes, involving an amount of RMB 100. More than 10,000 yuan. (8)
This sounds both similar to scams reported around the world. It is similar to the coin theft scam reported by Chinese victims active in the OTC market.
In the Chinese case, due to the differences in the legal systems of the two countries, it is not possible to provide Documents similar to those in the Florida and California cases are used for comparative analysis, but this does not diminish the similarities in the way the two countries work. As we can see, all the analyzed funds involved were laundered through wallets and intersected with service provider addresses, which proves a link between the two cases and that the fraudsters in both cases belong to the same criminal entity.
3 service providers
Florida victims' court documents mention four cryptocurrency exchanges: Binance, Bitkub, FTX and OKX, all of which Well-known large-scale service organization. Binance has long been the world’s largest cryptocurrency exchange, and FTX was founded by Sam Bankman Fried, who is currently awaiting the outcome of a high-profile fraud trial. OKX is a large cryptocurrency exchange that, while not as well-known as Binance and FTX, sponsors some of the most high-profile sports teams and events around the world. Bitkub, the smallest of the four listed companies, is Thailand’s largest cryptocurrency exchange and also has high-profile sponsorships within its marketplace.

Figure 1: The funds of the two victims in Florida and China are related, and the defrauded funds entered the same group of money laundering addresses. Note that this FX deposit address is not mentioned in the Florida filing - it is an additional downstream address.
Further analysis found that Coinbase, Huobi, Maicoin, Maskex, Paribu and Peatio all It is a similar well-known exchange. Coinbase is listed on Nasdaq, has annual revenue of billions of dollars, and currently has a market capitalization of tens of billions of dollars. Huobi is a large exchange with several subsidiaries listed on the Hong Kong Exchange, and like many other Asian exchanges, it sponsors sports including the Spanish men's national football team. Maicoin calls itself Taiwan’s leading cryptocurrency exchange. Maskex is a cryptocurrency exchange based in the UAE and holds a VASP license. Paribu is a Turkish exchange that has partnerships with several Turkish football clubs. Peatio is a Chinese cryptocurrency exchange that shut down and opened up their trading software a few years ago, and while the exchange may have gone out of business, its wallet addresses are still active.
Here, we just want to make sure that these service providers are large, well-known, Visible entities that are not required to undergo further analysis or provide any form of documentary evidence of their existence or involvement in cryptocurrency transactions.
Further discussion will involve the mechanisms operating between the fraud entry point and the exchange Smaller parties. Although these are less visible in the press and sports world, it is not difficult to find that exchanges are clearly involved in the management of fraudulent proceeds.
4 Downstream Fund Tracking
This paragraph analyzes the downstream addresses of the China case and the Florida case, revealing the final flow of funds obtained from the fraud. In Figure 1, we plot transfers from three addresses in Florida and one address in China, through the same intermediary address, to two wallets we labeled ml1 and ml2. ML stands for "money launderers," people who take proceeds from a series of scams and deposit the money into exchanges, which function as fund pooling addresses.
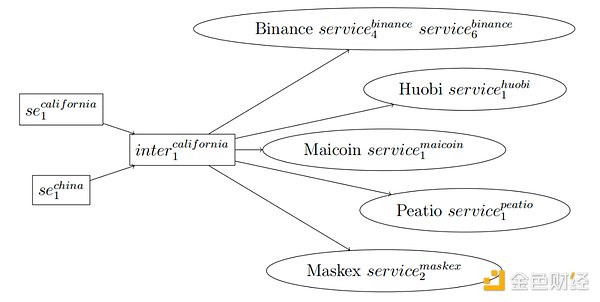
Figure 2: Compare the California scam address with China The scam addresses were connected and their shared downstream intermediaries were found to be connected to many exchanges.
It should be noted that fraudulent proceeds will not be transferred in a point-to-point, single-line sequential manner. are transferred via laundering addresses, and not every unit of fraud proceeds is delivered simultaneously through this exact sequence of wallets. Instead, we simply determined that these frauds and their subsequent money laundering occurred in similar ways and at similar times. Therefore, it is likely that these gangs are part of the same overall group. This is particularly compelling because the funds all ended up going to the same set of laundering addresses leading to the exit.
Now let’s connect the China case to the California case. In Figure 2, we see overlapping flows of funds in different cases – the same wallet appears downstream of two different cases.
Also note that the intermediary address inter.california is the same as the California case The civil forfeiture order (3) relates to a number of deposit addresses given. Furthermore, one of the Binance deposit addresses in Figure 4 was revealed by a Reuters reporter a few months ago and came to the attention of ChainArgos, as this address has been linked to a number of scams related to (6).
Next, we will show the intermediate addresses and exchanges in Figure 3 connect. The Chinese case fraud input address is also directly linked to the exchange deposit address in Figure 4.
A similar structure can also be seen downstream of se2.china. After creating an intermediate wallet, the funds are deposited into service5.okx.
While this is not an exhaustive representation of all addresses, it is still indicative of these scams They are all interconnected and spread to many exchanges.
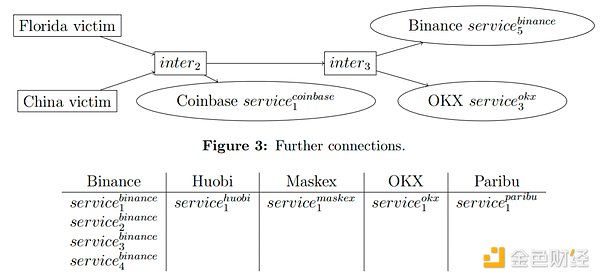
Figure 3: Fraud entrance address with Chinese victims Directly connected exchange deposit address.
5 total amount
This article so far has identified individual scams as part of a larger fraud organization by disclosing individual scams and tracing their common funding sources . Currently, there is not enough information to allow us to document all scams perpetrated by this or related groups. Given the nature of the crimes and the victims, it is difficult to have a reliably exhaustive list. Therefore, the next logical step is to look at the total amount of funds from the service provider addresses used in these cases to determine the potential size of the organization. Analysis of the funding size raises three separate but related questions:
1 . How much money has flowed into the disclosed “scam entry” addresses?
2. How much money is transferred through the service provider?
3. How much money flows to capital outlets like exchanges?
5.1 Scale of the scam
We found that from the beginning of 2021 to the time of writing, a total of 20.7 million US dollars had flowed through China as disclosed earlier The relevant address of the Tianjin victim case. Since the victim lost about $40,000, we only focused on a small part of the gang's criminal activities. It is certain that more funds involved will be concentrated at this address.
In the Florida case, the victim claimed losses of approximately $2.2 million, but this The total inflow from the three addresses was just under $6.5 million, confirming that there must be more victims. Of the six "scam entry" addresses used to map this traffic, we found that the total inflow was:

< span style="font-size: 18px;">What is most unique among these addresses is that most of the fraudulent funds flowing into se1.california were denominated in Ethereum rather than the stablecoin USDT. In total, se1.california received Arrived at 156.04 Ethereum coins. We dollarized Ether at $2,000, which reflects the average conversion price at the time of transfer.
5.2 Service provider scale
Next let's look at the total amount of traffic passing through some intermediate addresses. For the six intermediaries in the above example, we find that the inflows of USDC and USDT are:

Some of these are the same tokens flowing through multiple addresses, and the example even shows a flow from ml1 to ml2. Based on reasonable traffic estimates, these intermediaries handle amounts between $80 million and $100 million.
So far, the largest flow of funds has gone to exchanges. By checking the deposits to the exchange address specified in (1), we find the following totals:

If we add the address connected through other cases, we get:

While this does not mean that this criminal organization is responsible for all of these assets, it provides strong evidence that there is still a large amount of criminal liquidity in the area yet to be discovered.
Please note that these data include several transactions with low transaction volume. These are included for completeness of data and are not intended to be exhaustive. Even on exchanges with larger totals, we find that individual deposit addresses will have different orders of magnitude in total traffic.
Also note that almost all trading volume occurs outside of China and the United States Exchanges are, overwhelmingly, handled by businesses based in overseas jurisdictions.
5.3 Exchange Withdrawal
In the California case, the investigation also found that a fraud gang controlled the Tron block. An exchange withdrawal address with approximately $1.1 million in funds passed through this Tron address far exceeds the approximately $500,000 lost in the California case, suggesting that further investigation into Tron and other blockchains may uncover more Lots of correlation clues.
6 Discussion
This analysis demonstrates three key facts:
1. Similar simultaneous scams have victims in China and the United States;
2. Funds withdrawn from two jurisdictions circulate through a common intermediary address;
3. The amounts involved range from tens to hundreds of millions of dollars.
It is important to understand the following limitations of the analysis:
1. We are not saying that the $30 million flowing into these "scam address" wallets is Scam income is only what can be tracked currently;
2. Although discovered $635 million in foreign exchange deposits, but we’re not saying all of this can be attributed to a scam;
3. Considering the cycle of transactions, the above figures may not be completely free of double counting.
*For example, some money deposited on an exchange may be withdrawn and Restore elsewhere.
Instead, the analysis should be understood within the context of the scope and scale of the fraud being committed. First, only four cases were analyzed in which victims came forward and initiated some form of formal legal proceedings. Second, we have shown that these scams are related to the scam discussed in (6), suggesting that the scale and scale of such scams may be deeper and more widespread than previously understood.
There appear to be more clues to the flow of money yet to be discovered through the cryptocurrency ecosystem The proceeds from the scam may be much greater than our current estimates. Furthermore, it is worth noting that while the victims of these cases are located in two of the world’s largest economies, at most only a small fraction of the exchanges handling the proceeds of these scams are located in these countries. In order to solve these problems, a lot of international cooperation is needed.
References
[1]Bowenv.XingzhaoLi,23-cv-20399-BLOOM/Otazo-Reyes(S.D.Fla.Jul.26,2023).< /span>
[2]China Ningbo Net.A large amount of virtual currency was stolen from a ningbo citizen by a hacker., 7 2022.
[3]Florida Circuit Court . Eighteenth Judicial Circuit In And For Brevard County, Florida Case No: 05-2002-CA- Filing 162250539 Civil Forfeiture.
[4]Global Anti-Scam Alliance.The global state of scams - 2022 report, 2022.
[5]Ledger. Security incident report, 12 2023.
[6]P. McPherson and T. Wilson.Crypto scam: Inside the billion-dollar ''pig-butchering'' industry.11 2023.
[7]ScamSniffer. From google to x ads: Tracing the crypto wallet drainer''s
$58 million trail, 12 2023.
[8]Wenzhou Public Security Bureau.743 cases were solved and 2,093 people were arrested! the resultsofthewenzhoucleannetwork2022operationareannounced!,112022.
[9]ZachXBT. Monkeydrainertwitterthread,102022.
Appendix: Address

 JinseFinance
JinseFinance













